AWS Security Assessments
Why you should get an AWS security assessment
Whether you have one AWS account or over a hundred, I can audit your AWS accounts to look for security concerns. Similar to a pentest, at the end you'll have a document with all issues found, prioritized, and with recommended steps for fixing the issues and steps for testing to ensure the problem has been resolved.
I'll look for a large number of issues specific to AWS both through automated tools and manual investigation. In addition to public S3 buckets or access keys that haven't been used in over 30 days, there are a large number of other issues that will be checked for.
This report will also include:
- Statistics about the AWS services used in the accounts.
- A diagram of the trust relationships between these accounts and potentially unknown acounts.
- A list of who the admins are in the accounts.
- Network service fingerprints of publicly exposed ports and screenshots of public web services.
I can also advise improvements to your least privilege strategy based on historic usage of users and roles in your accounts.
Having an AWS assessment performed helps double-check assumptions or helps you to understand the state of other accounts at your company that you don't currently have much insight into.
I'm commonly brought into companies prior to funding rounds to ensure due diligence has been performed, by new heads of security wanting to get a lay of the land, or I perform assessments before working on larger projects for companies to ensure their environment is free of misconfigurations.
If you haven't already, contact Scott today about scheduling an assessment.
What to do to prepare for an assessment
Identify all of your AWS accounts
Before an assessment begins, you should know what AWS accounts you have and who the points of contacts are for them. For advice on identifying accounts at your company and the information you should collect about them, see How to inventory AWS accounts.
Granting access
To assess accounts I need some access to them. The access is view only, meaning I can see the metadata about the account, but cannot change anything and do not have access to the data in the account.
My preferred access is via cross-account trust to a role created in your account. We can work out other solutions as long as I can get session keys to run scripts.
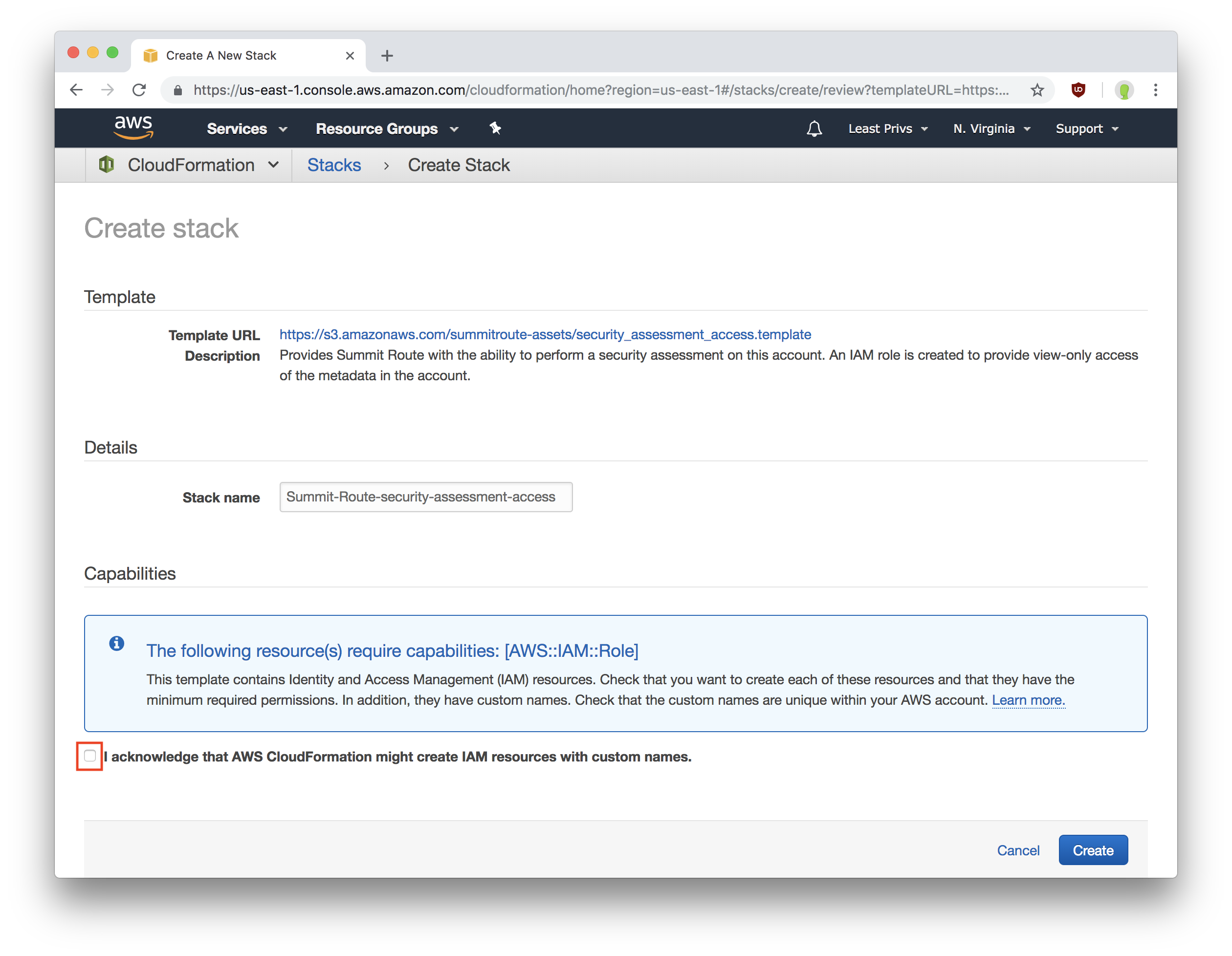
While logged into your AWS account, you can grant Summit Route access by clicking on this link:
The CloudFormation template can be seen at: https://s3.amazonaws.com/summitroute-assets/security_assessment_access.template
This will show you this page:
If I'll be performing a least privilege analysis, provide the name of the S3 bucket containing your CloudTrail logs in the first box.
Click the checkbox to accept the access to be granted, and click "Create".
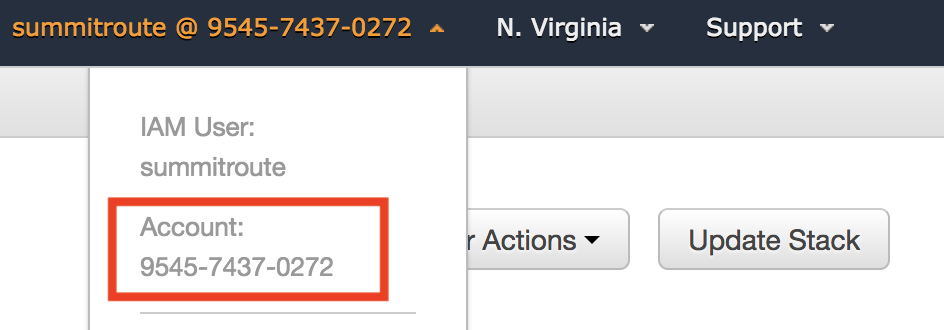
It will take a few minutes to create the access, at which point you'll need to send Scott your 12-digit account ID which can be found by clicking on your username in the top right corner of the AWS console, and a name you use for this account, such as "prod", "dev", etc..