In April of last year, John Lambert wrote Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win. Despite it’s polarizing title, that article does helpfully explain the concept that there are trust relationships within your network that can give an attacker access to your high value assets.
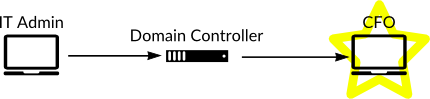
Let’s assume the most important asset in your network is your CFO’s laptop, because if someone gained access to it, they could steal all your company’s money. You could do whatever you wanted to lock down that laptop, but most pen-tester’s will tell you if you can get access to the Domain Controller, you can get access to this laptop. So you need to lock that down too. But as Microsoft has recently been advocating with their Privileged Access Workstation, if you can get access to the IT guy’s laptop that he uses to connect to the Domain Controller then you can ultimately access the CFO’s laptop, so you need to lock down that asset too. Therefore, gaining access to any one of those systems is equivalent to gaining access to the CFO’s laptop.
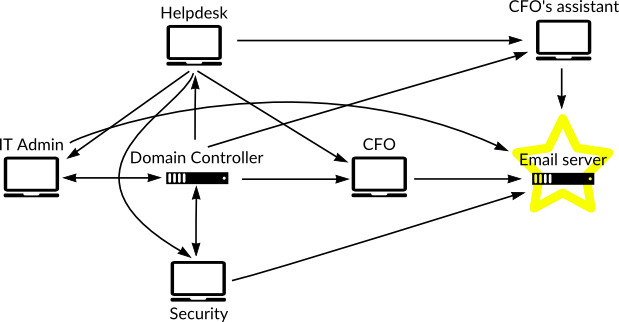
That’s just one path though, and one abstraction of what the important thing is you’re trying to protect. What you actually care about might be the email of CFO, and so you need to protect the email server and anyone who has access to it, along with others who also have access to the aforementioned systems. This means you need to you protect your helpdesk who can change people’s passwords and/or remote into people’s computers to fix problems. You need to protect the systems used by your security team who likely has access to your servers, and potentially, through the tools they use, has access to everyone’s laptops as well. You need protect the assistant of the CFO who has access to the CFO’s email to help filter them. We now have Figure 2 showing all these relationships, which shows that access to any of these systems is equivalent to access to the CFO’s email.
There are likely more tools and assets that just compound this problem. This problem isn’t isolated to the control you have over your own network though. Businesses use many software vendors. More than just the Microsoft, Apple, and Google that the home user may be exposed to. Many software vendors, through their software’s updates, have access to the assets on your network. These software vendors in turn use software from other vendors. So your graph looks something like Figure 3.
Don’t stare too hard at that graph, since I just drew a bunch of lines at random to express the idea that many businesses are inter-connected with one another.
Halvar Flake touched on this recently when he said
“Control of the software and update infrastructure are the most crucial strategic weapons a nation can acquire.”
Although I titled this post “The Great Graph” as an allusion to The Great Game (ie. espionage), this is not just the game of states, and it has been happening with criminals since before computers even existed. In “The Oil Barons: Men of Greed and Grandeur” by Richard O’Connor, he mentions an account of how someone looked for places to drill for oil in East Texas around 1930:
“First, to save trouble, I tried to bribe the man who tabulated the findings of the seismograph crew to give me the information I wanted. I did it subtly so that he could take it or leave it and not have an obvious right to be offended. If he didn’t choose to be bribed, I then had his maps stolen. That failing, I bribed the map maker who struck off duplicates for the oil company. If that didn’t work, I bribed the archivist in the oil company office. He didn’t have to steal them for me. I would be satisfied with a photostatic copy.”
A new era of exploitation
I contend that we have been entering a new era of exploitation, focused on exploiting trust relationships rather than programming flaws in software. This isn’t to say that this hasn’t been happening previously, or that other forms of exploitation won’t continue to happen, but simply that the focus shifts from one area to another. Attackers focus on weak spots, and attack until defenders sufficiently improve that area to cause attackers to look elsewhere.
The first era of exploitation was server exploitation, with high-lights such as the Morris Worm and various worms of the early 2000’s such as Blaster and Sasser. Then we entered the era of client-side exploitation with Java, Flash, Adobe Reader, and browser vulns. That transition occurred around 2004 when Windows XP SP2 came out which added a firewall to Windows. Workstations were also being put behind minimally NAT devices, which effectively staunched those worms.
I noticed in 2013, that we were at a transition point away from the client side exploits because Java, Flash and Adobe Reader were being killed off, but I didn’t know what the next era was. I believe it has been to this exploitation of trust. Client exploits will continue, as have server exploits, and exploiting trust has always existed with computer networks. This is just what I view as becoming a more predominant concern.
Examples
Trust exploitation can be thought of as a supply chain problem in many ways, but with continuously delivered software and connections between networks that aren’t deliverables, it’s more than that. Let’s look at some examples:
- The Target breach in 2014 involved the breach of an HVAC contractor that was leveraged to breach Target. Link.
- Pager Duty was breached in 2015 because it’s servers ran on the cloud hosting company Linode which was breached. Link.
- Juniper routers were recently discovered to have had backdoors inserted in them, which has likely led to undiscovered breaches at many of Juniper’s customers. Link.
- A copy of the Apple Xcode IDE was trojaned and this made it’s way into many app vendors, resulting in trojaned apps being pushed out to hundreds of millions of users. Link.
- The auto-update server of Puush, a screenshot application, was hacked and used to push updates to all it’s clients containing a RAT. This hack even hid itself by using GeoIP data on the connecting clients to avoid infecting systems in Japan where Puush is based. Link.
- Samsung was breached because a company it purchased, named LoopPay, had been breached and then integrated into Samsung’s networks. Link.
In all these cases, in the second stage of the attacks, no “exploits” were used. No buffer overflows or SQL injection. There were no programming flaws. Only trust was exploited.
What to do
The article The Hierarchy of Cyber Needs lays some important groundwork by pointing out that you need to know what is on your network, in terms of devices, software, and people. Know the accesses these have and prune and limit these as much as possible. Know the connections coming into your network and where your data and services live and what potentially has access to those places. This is a hard problem, and is where my attention is being drawn.