Virus Bulletin (VB) is an annual conference that takes place in a different city around the world, and this year took place in the city I work in, Denver, Colorado. I was lucky enough to attend on a Press Pass (finally writing this blog did something for me!).
Virus Bulletin is a professional conference for AV companies. It doesn’t bring in the .gov employees or pentest crowd. I would guess over three quarters of the attendees were not from the US. The conference is on the smaller side with only a few hundred attendees. There were only handle of booths of vendors, with one of them being a company to provide Tier 1 tech support for customer help tickets. No one laughed at the rare jokes attempted by the presenters. With some exceptions, the presentations are largely from people’s actual daily work, not some side project they do on weekends or that their company funded specifically in order to do something worthy of a press release. This meant most of the presentations were not focused on junk hacking or buzzfeed worthy announcements. The focus of this conference is mostly malware analysis and improvements in categorization.
The first two presentations I saw were from Kaspersky and then a joint presentation from Cymmetria and Perimeter X. Both of these talks were about the false flags being used by APT actors. Kaspersky took a strong stance that end-point security companies should not be attempting attribution, and that activity should only be done by governments who both have the additional types of info and access needed to make those claims, and also who benefit from those claims (they can take action against countries). Cymmetria and Perimeter X followed this up by saying most APT reports really only benefit the attackers, and have very little information in them that is useful for defenders. Its just free QA and notes for improvements to the attackers to avoid being caught in the future. These reports have also led to a decline in shame. When the APT 1 report was released, that actor shut things down for a while, but you don’t see those same responses anymore. Actors change some things to avoid being detected easily, but continue unabated.
The types of false flags and opsec activities of the actors were interesting. Kaspersky has a write-up of their presentation here. In one case, of an assumed Russian APT actor, it identified researcher systems running the first stage malware, so it sent down Chinese APT to the researchers as the second stage to throw them off, while sending down their real second stage to the actual victims. In a similar case, when Turla (also Russian APT) worried they’d been detected, as they were pulling out their malware, they sent down a rare Chinese malware named Quarian for the IR team to investigate. This both gave them time to cover their own tracks, while at the same time burning China’s toolset.
My main interest at the conference was to learn about advances in macOS attacks, which the speakers on this subject all mentioned are far less mature than the Windows side. Patrick Wardle of Synack, and his own project Objective See, mentioned how three known malware samples have had functionality to access the webcam. With modern macOS laptops the webcam light will indicate when monitoring is occurring and would be extremely hard to circumvent (the firmware is signed, so you’d need to target the chip manufacturer or Apple). However, if the webcam is already in use for something else (a Google Hangout, Facetime, etc.) malware could detect and piggyback on that session. Patrick therefore released a new tool, Oversight, to detect processes using the mic or webcam.
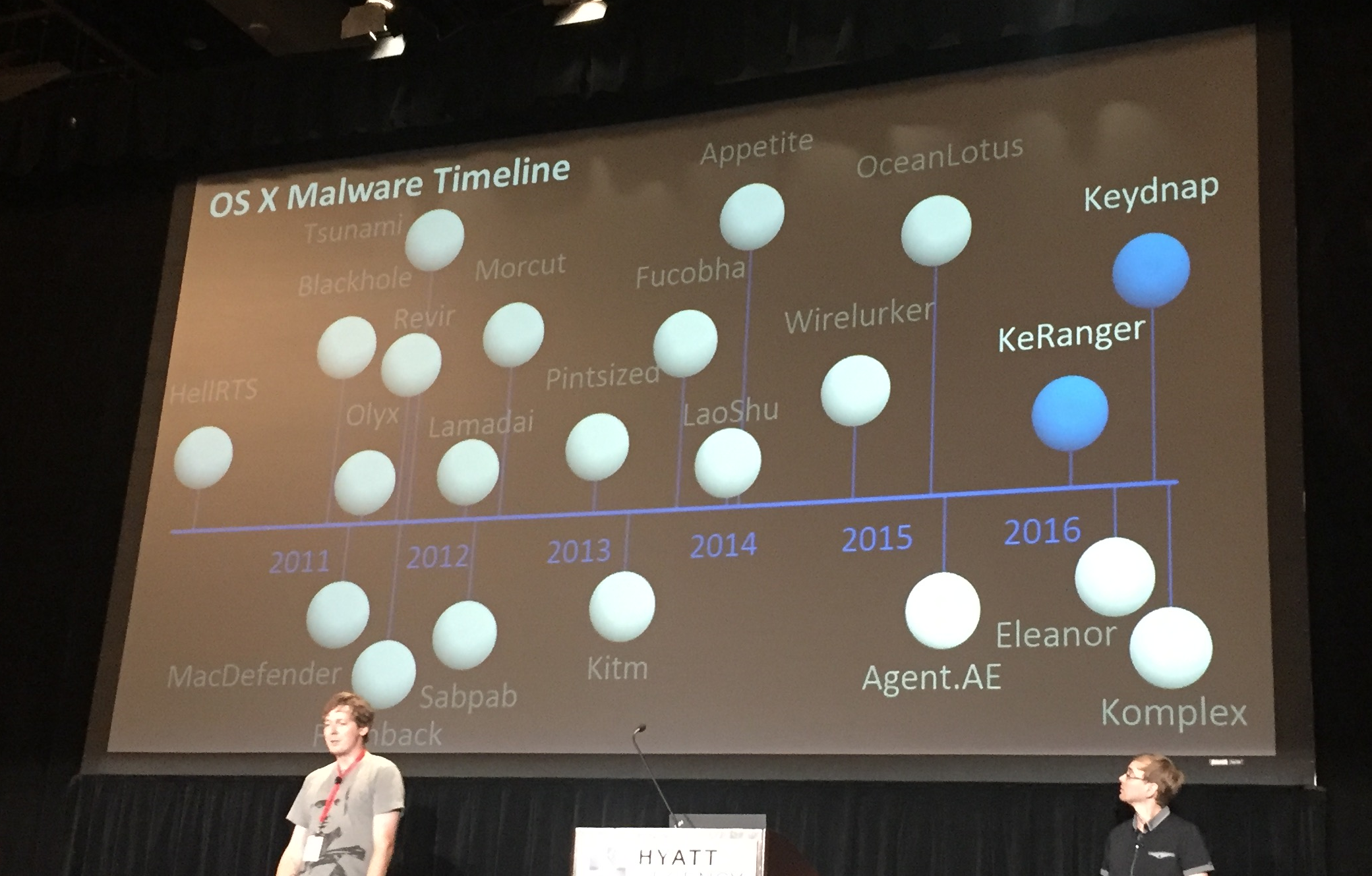
The timeline picture above is from ESET’s talk, where they discussed malware this year, KeRanger and Keydnap, that had been pushed down through the Transmission app for OSX. Giving some stats that those attacks were largely ineffective (they hit few systems and were discovered and remediated quickly) and the attacker didn’t actually do anything against those systems (didn’t send any commands). One interesting bit was they said that Keydnap has functionality to monitor when other applications and started and then present a password prompt to the user to trick them in order to escalate privileges. A trick somewhat similar to what scriptjunkie released a POC for recently in his post Intercepting Passwords to Escalate Privileges on OS X.
Trend Micro had a good presentation called “Operation Sentry Stopper” about an espionage attack happening in China against their financial sector. Instead of hiding from AV, the malware attacked the AV to cripple it in two ways. The first was to make an NTFS junction point against the AV’s install location, and then write an older version of the AV’s scanner engine to the location. This ensured the AV wouldn’t notice the attack, while it was being crippled down to an older, weaker engine. The other trick was mark the AV’s signature database as read-only so no new updates could be applied.
Noticeably missing from the conference was a talk by Tavis Ormandy who has been finding flaws in AV products this year and was supposed to present. However, the closing keynote, from Morgan Marquis-Boire of Citizen Lab, high-lighted Tavis’s work, giving multiple screenfuls of bug reports from Tavis. Morgan also mentioned the past work from Alex Wheeler, Neel Mehta, and Joxean Koret (picture above) and commented on the irony of how AV products are not undergoing the same rigorous auditing or secure development practices as other software does.
This was a great conference to learn about the advances in detecting, reversing, and analyzing malware and its campaigns. Although the conference is made for end-point security employees, it’s also valuable for blue teams to learn some of the inside baseball that these companies discuss.