A month ago I added support to CloudMapper for private commands which I’ve used in work with clients. These are just commands that can be added to a directory named private_commands and can be called in the same way as other commands, but this directory hides behind a .gitignore line so I don’t accidentally push this code. My goal with my consulting business is to continually improve AWS security for everyone, which includes open-sourcing useful code, but I needed a sandbox to develop things without introducing too many problems into the main code base. Today I’m releasing one of the commands I developed recently which will be the basis of a report.
When I first start working with a client, one of the things I want to do is get a high-level understanding of their different accounts. This new command named report shows a couple of graphs and tables to help me. Clients have also found this useful for giving them new insights into how their accounts are being used.
A demo report can be seen at https://duo-labs.github.io/cloudmapper/account-data/report.html
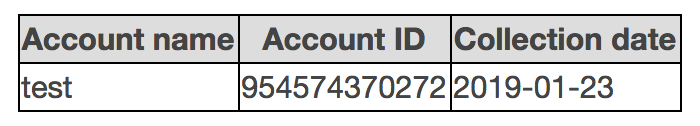
The first table is a list of the accounts (names and IDs) and when the collect command was run against them.
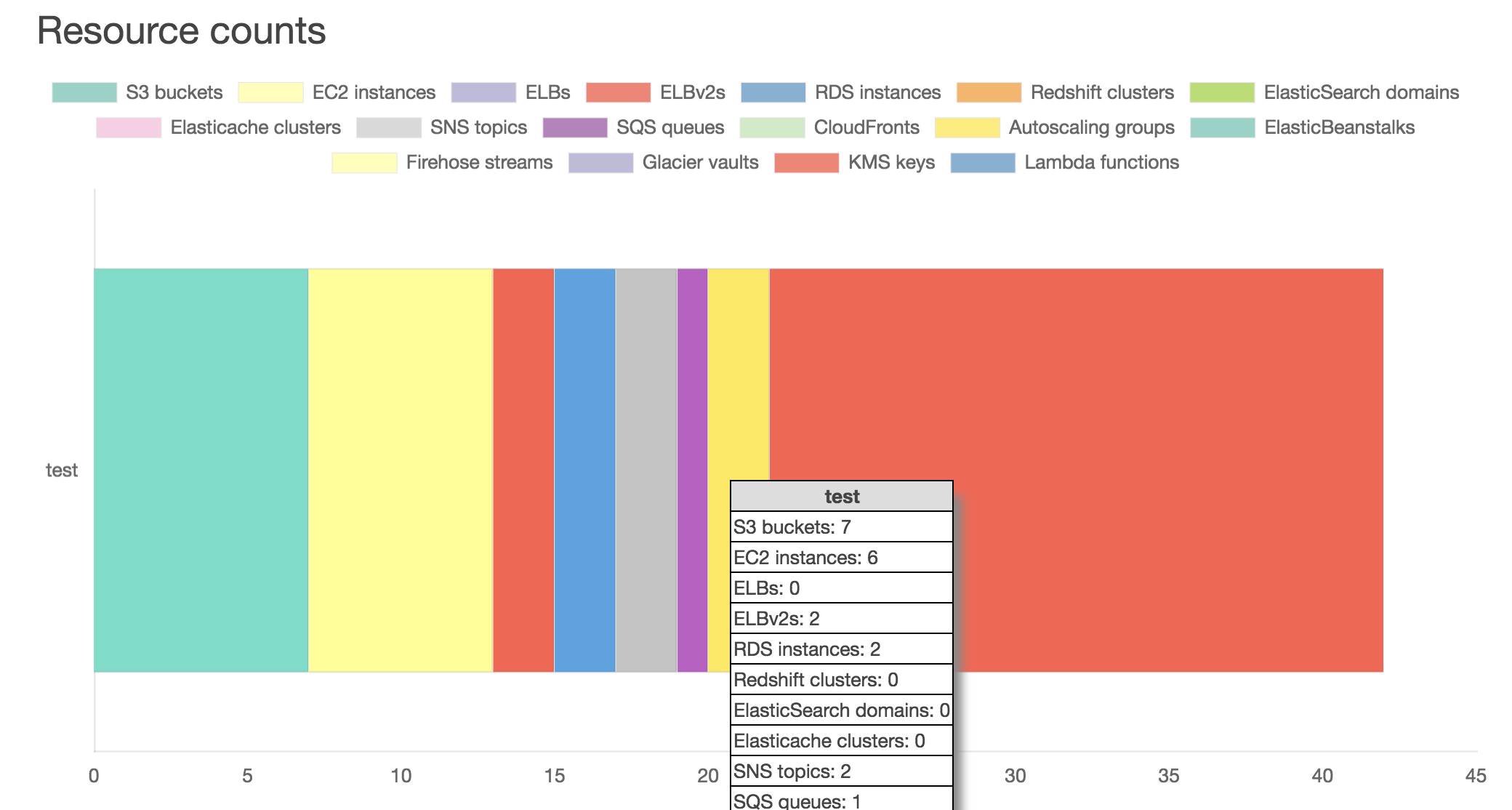
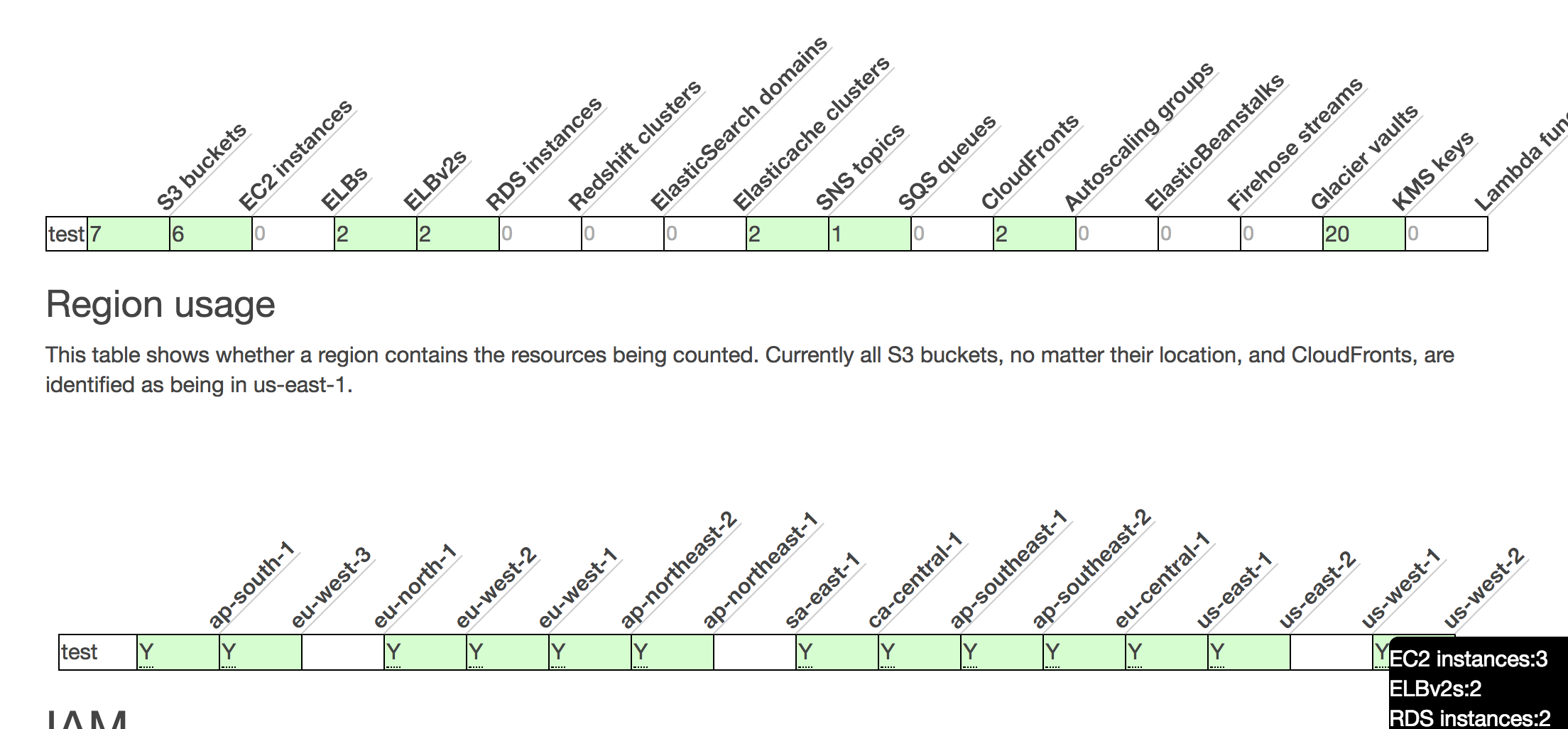
Next, there is a chart and tables to show the counts of resources and what regions those resources are in. This can quickly show you what the “biggest” accounts are, and by just how much. The chart and some of the table data is interactive, giving you more details, or in the case of the chart, you can click on the resource to hide it from being displayed.
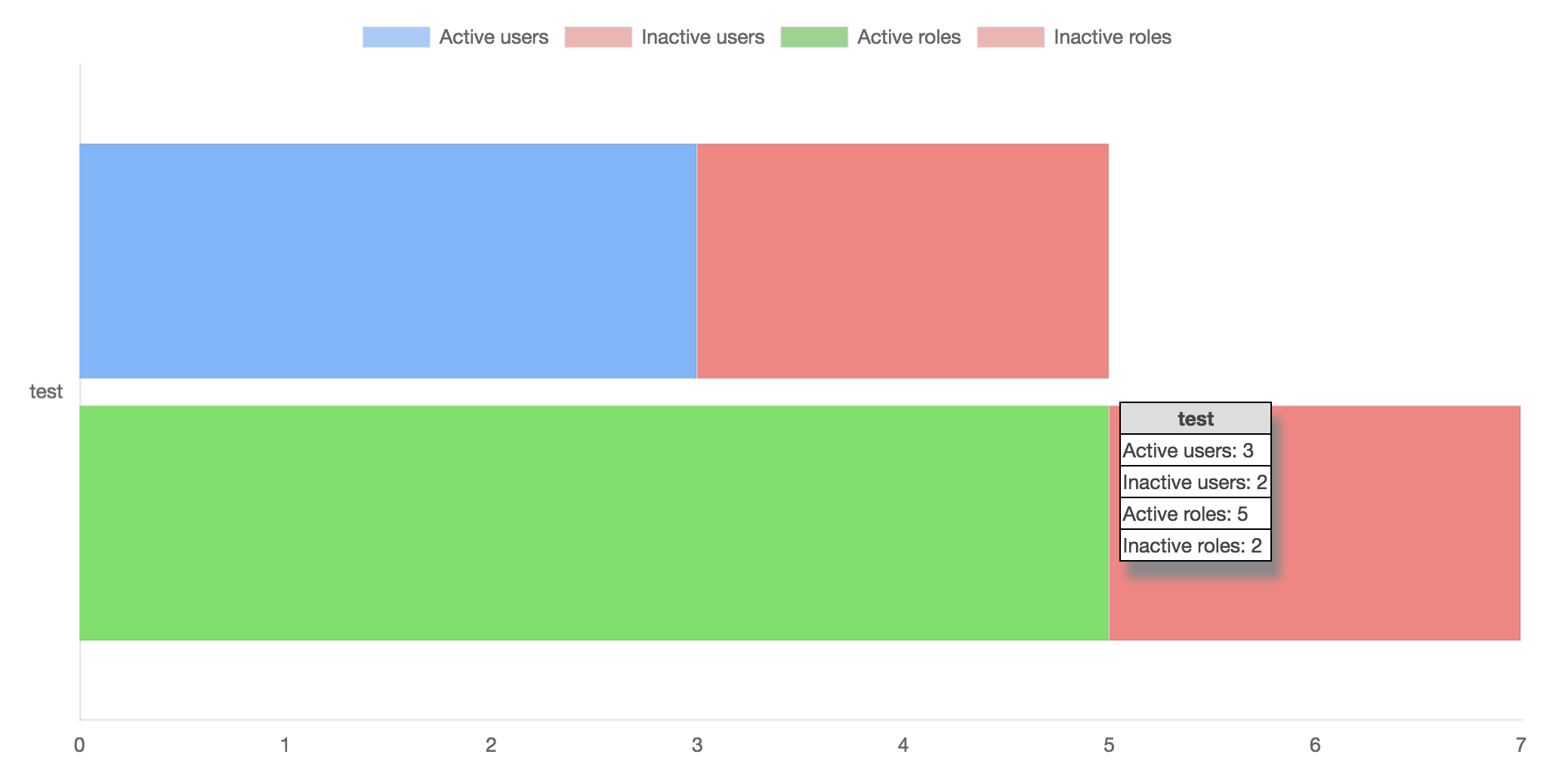
Next, there is a chart of the IAM principals. This show not only how many Users and Roles are in the accounts, but by using the new Access Advisor APIs that are collected, it shows how many of those principals haven’t been used for 90 days. Each account has two bars, one for the Users and one for the Roles, and ideally you don’t want to see any pink, which indicates inactive Users and Roles that can be removed (I’ll release another command soon that identifies exactly which principals are inactive). Current best practice on AWS is also to not have any IAM Users, so this can also show you how many Users you have if you start working to reduce those.
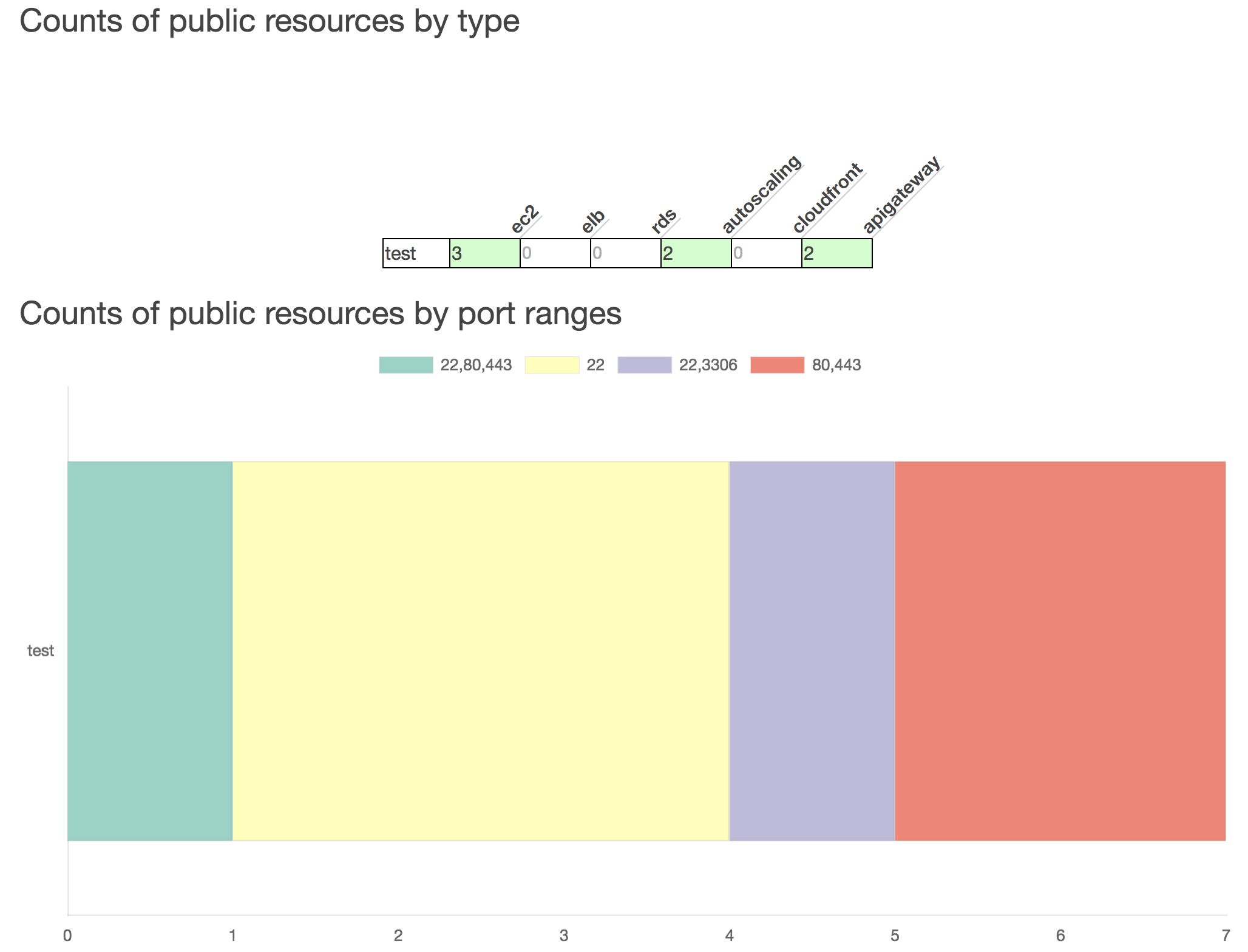
Next, there is a table of the public network resources, and then a chart of the port ranges that the public network resources have open. You can dig deeper into that data by running CloudMapper’s public command.
Let me know if this new command has been helpful to you!