I’ve been writing Downclimb, my weekly infosec news summary, for 3 years now. One of the reasons I do it is to try pass on my knowledge to improve infosec. I believe Downclimb differentiates itself from all the other news resources by highlighting how you can avoid problems, events that indicate a change that you should react to, tools that you can use to improve your defenses, and generally focusing on news things that you can act on.
This isn’t entirely selfless though: I need security to improve everywhere. Now more than ever, as I mentioned in my post The Great Graph at the start of 2016, we are facing attacks from indirect targeting. In the past few months we’ve seen NotPetya and ShadowPad each target one company in order to compromise others via their auto-updates. These attacks are difficult to detect and defend against. Although NotPetya is now believed to have caused roughly a billion dollars in losses, the attackers could have done much worse with the access they had. For every company that experienced losses from NotPeyta, the attackers had control of systems at those companies for 4 months before anyone noticed, and the only reason anyone noticed was because the attackers chose to make themselves visible.
In order to really drive home the point about the ecosystem we all live in now, I’ll use a simple example, drawing from some comments I’ve heard pointing out the dangers if Twitter were compromised as it is now used for official government statements. Any company would work for this exercise.
So let’s assume Twitter is doing everything right with regards to security so they are a very hard target. Well, how might one attack them by compromising a weaker target? To put this another way, what are the trust relationships that Twitter relies on?
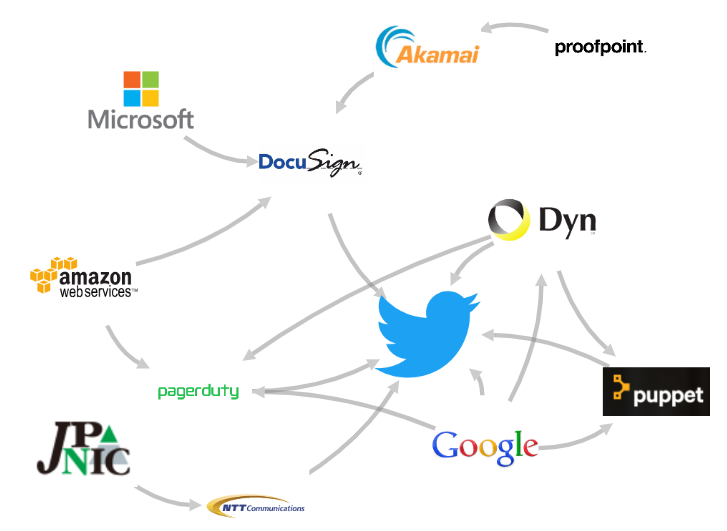
A couple of commands at the keyboard, and some mentions online about them using PagerDuty, Puppet, and Docusign results in the following graph of a subset of the ways that Twitter could be harmed by compromising other companies. The real graph of trust chains for Twitter, or any company, likely involves thousands or more nodes and edges, all of which have their own trust relationships, creating the massive ecosystem of our world-wide economy.
To get this graph, I first ran dig twitter.com ANY and found:
- They use Dyn as their domain registrar, as identified by the dynect.net SOA record. If an attacker compromises Dyn, they can point
twitter.comto an IP the attacker controls and may be able to obtain new SSL certs and steal passwords from users or redirect mail in order to run password resets on employees in order to compromise further accounts. - They use G-Suite (gmail) for their corporate email, as identified by the google.com MX records. Again, they can run the aforementioned password reset attacks.
Visiting twitter.com in your browser, you can see it pulls down javascript from twimg.com, and the DNS A record for that is 210.163.219.24 which a whois shows is owned by NTT Communications (some Google searching will also show you that NTT Communications hosts twitter’s server, link). So if an attacker compromises NTT Communications they can compromise the servers that host twimg.com, insert their own javascript, and again take over user accounts, or simply display arbitrary content on Twitter.
In 2015, PagerDuty was compromised by a similar attack as one of their hosting providers, Linode, was compromised. The compromise of PagerDuty in turn was likely going to be used to compromise yet-another company since the attacker would have been able to disable any alerts the next victim tried to send as it was attacked.
Some searching around online shows Twitter likely use PagerDuty. A post about Twitter’s engineering shows they use Puppet. If Puppet’s software was somehow backdoored, it could potentially lead to Twitter’s servers being compromised.
There are many vendors that if hacked would either lead to the compromise of Twitter or at least cause problems for them, and I’ve barely touched on all the vendors Twitter likely has or could be quickly discovered. Those vendors themselves have vendors. I showed a few of those relationships in the graph for which DNS registrars, mail services, and hosting services, different companies are using. One way to discover these vendors would be to compromise something like Docusign which is used, among other things, to keep track of vendor agreements. Again, some comments online mention Twitter likely uses them.
So you see, in order for any company to secure itself, it needs many other companies to secure themselves. You can take some steps to mitigate the impacts of different vendors being compromised, but ultimately I need all companies to be secure. So that’s why I write Downclimb.