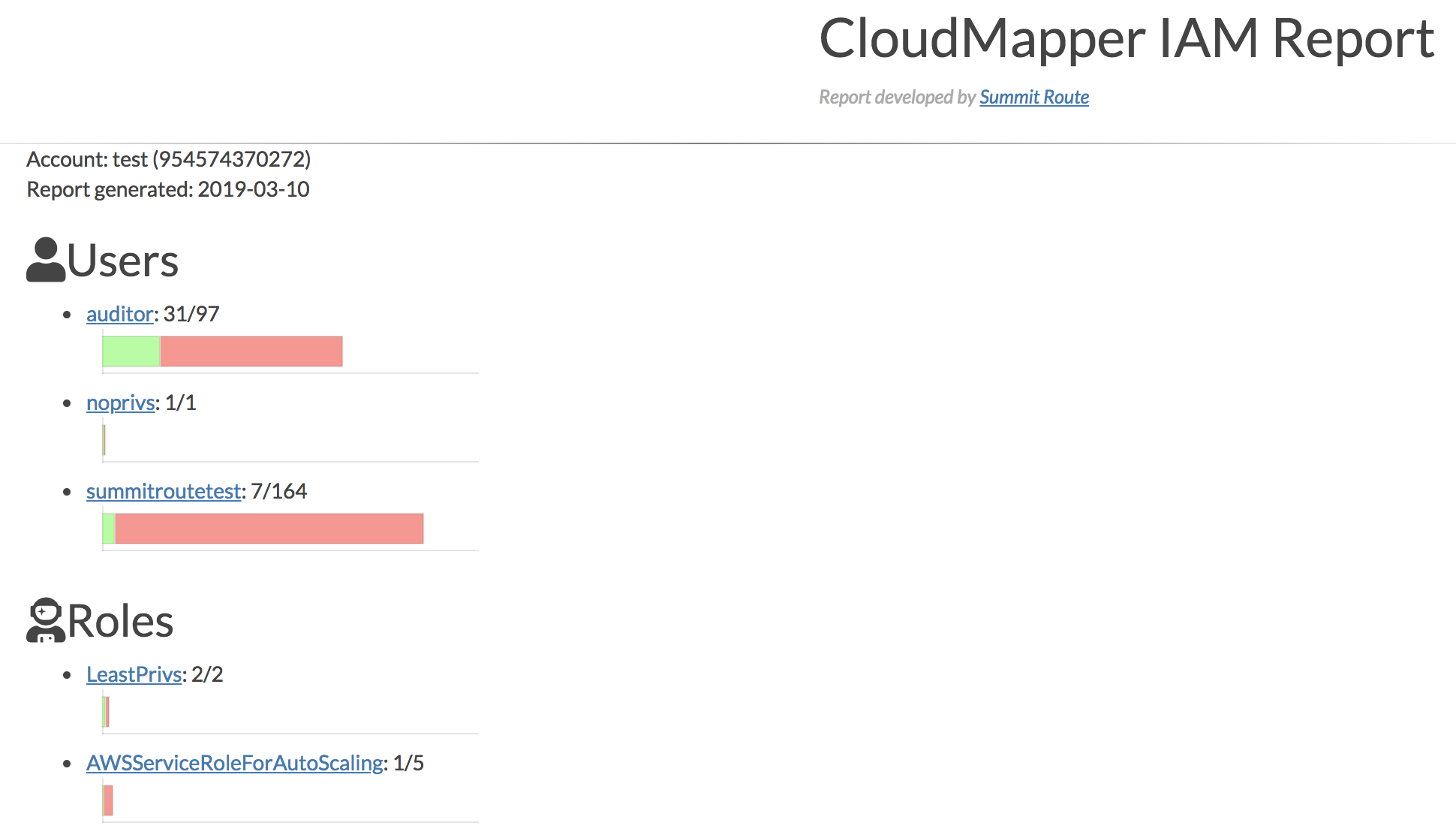
In order to help with manual auditing of IAM usage in AWS accounts, CloudMapper now contains an iam_report command which will generate an HTML report to collect much of the IAM information contained in an account. The command starts off by showing you all of the IAM users and roles in the accounts that have been used in the past 90 days, and uses Access Advisor data to show you a chart of how many services these principals have been granted access to and how many of those services have been used.
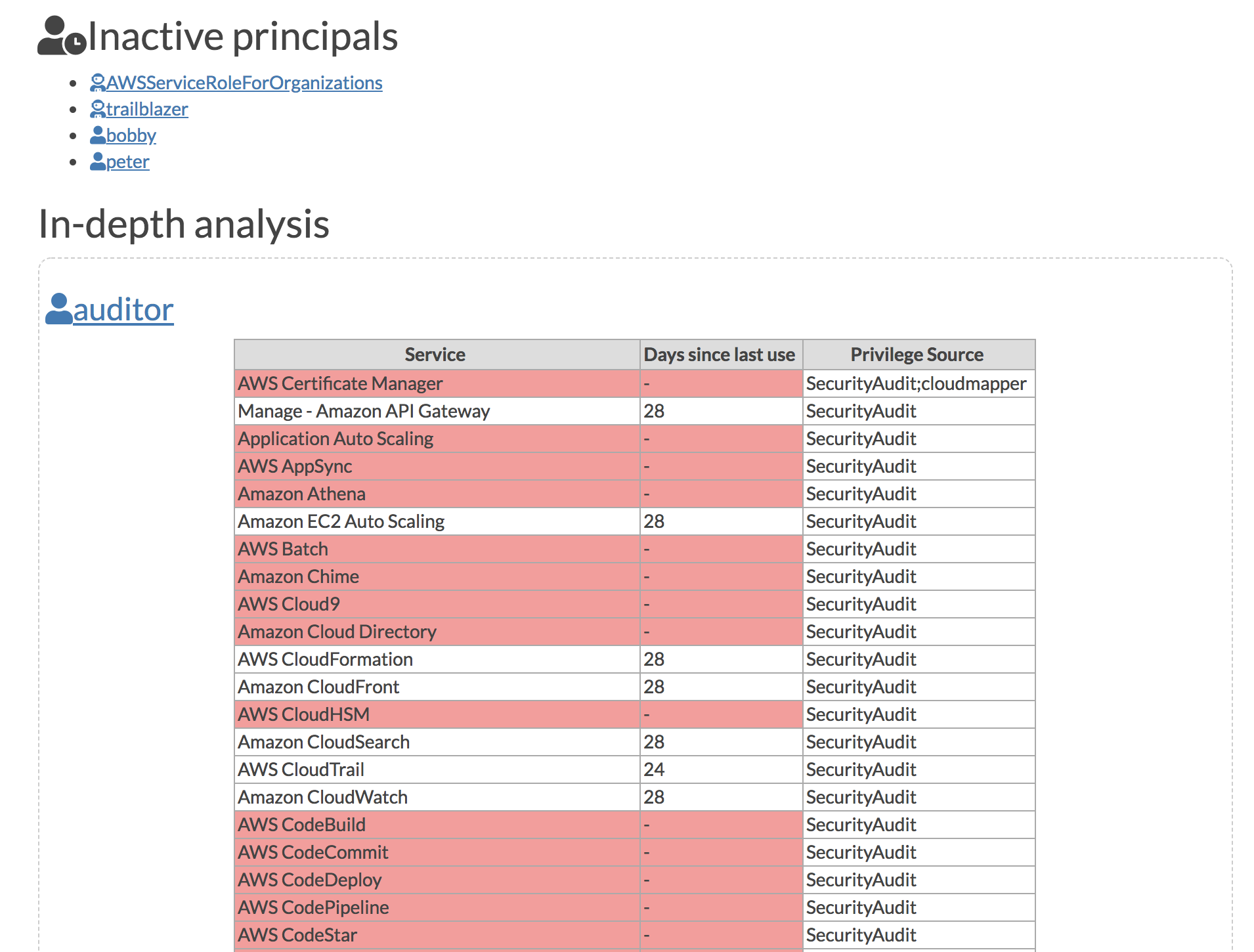
The report then shows the list of inactive principals (those that have not been used for 90 days). Then it shows detailed information about the principals, begining with information from Access Advisor to show the specific services that have been granted, when they were last used, and then where these privileges came from. This also shows any group membership, links to the attached managed policies, and shows the inline policies. Later the groups and managed policies are shown along with their members or attachments.
This report gives you most of the IAM information for an account in a single page to make it easier to search through. Attachments and memberships are linked betwene parents and children to make it easier to navigate and save you clicks if you were to look at this info in the UI, and saves you from having to make lots of command-line calls and dig through json if you were to do this from the CLI.
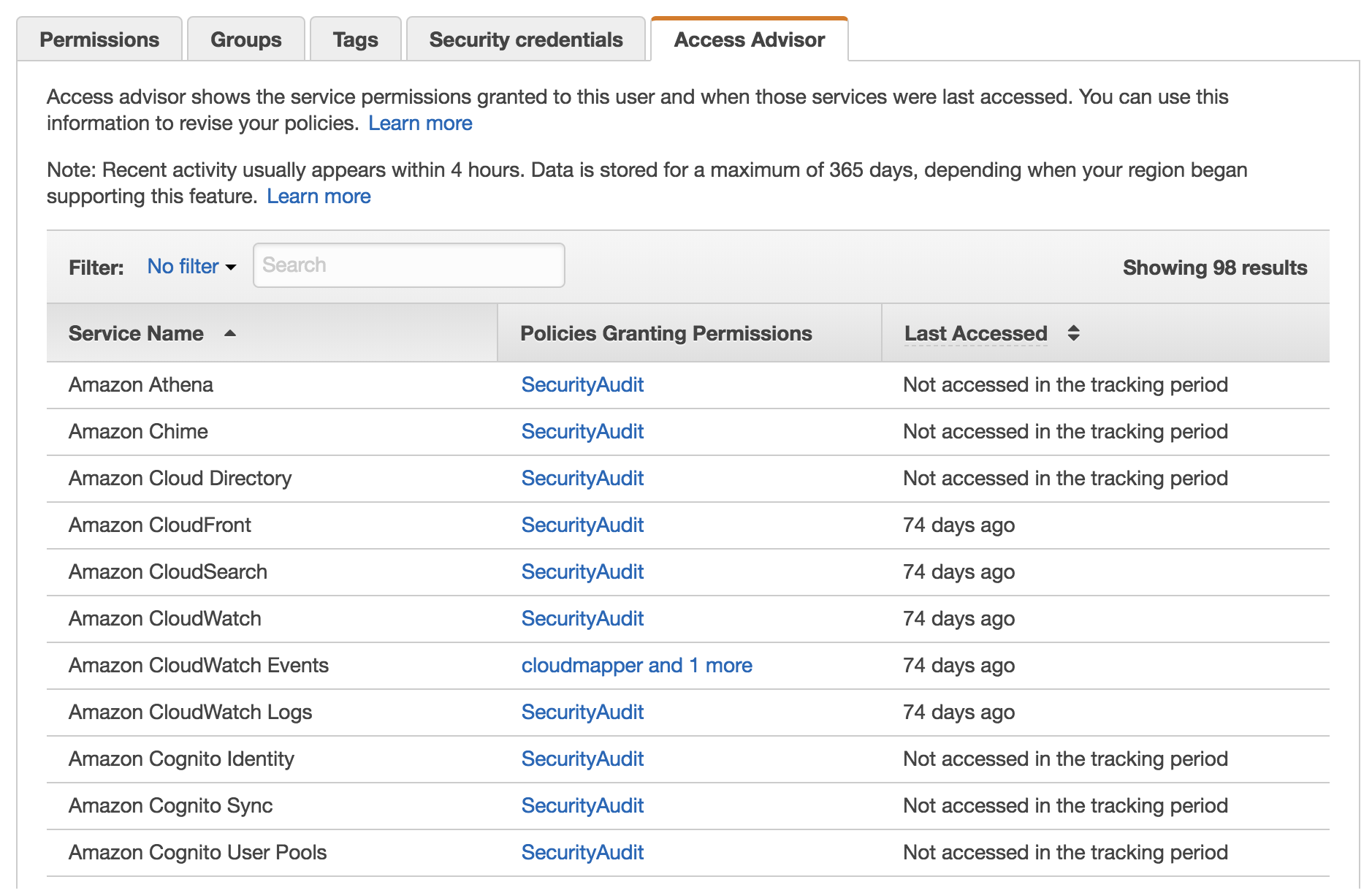
By comparison the screenshot below is from the web console, where you can see much of the same information.
By having my own report, I’ll be able to add additional information. For example, a future update could better identify which privileges within a service have been granted, so you can narrow in on only those privileges that allow changes if that was of interest.
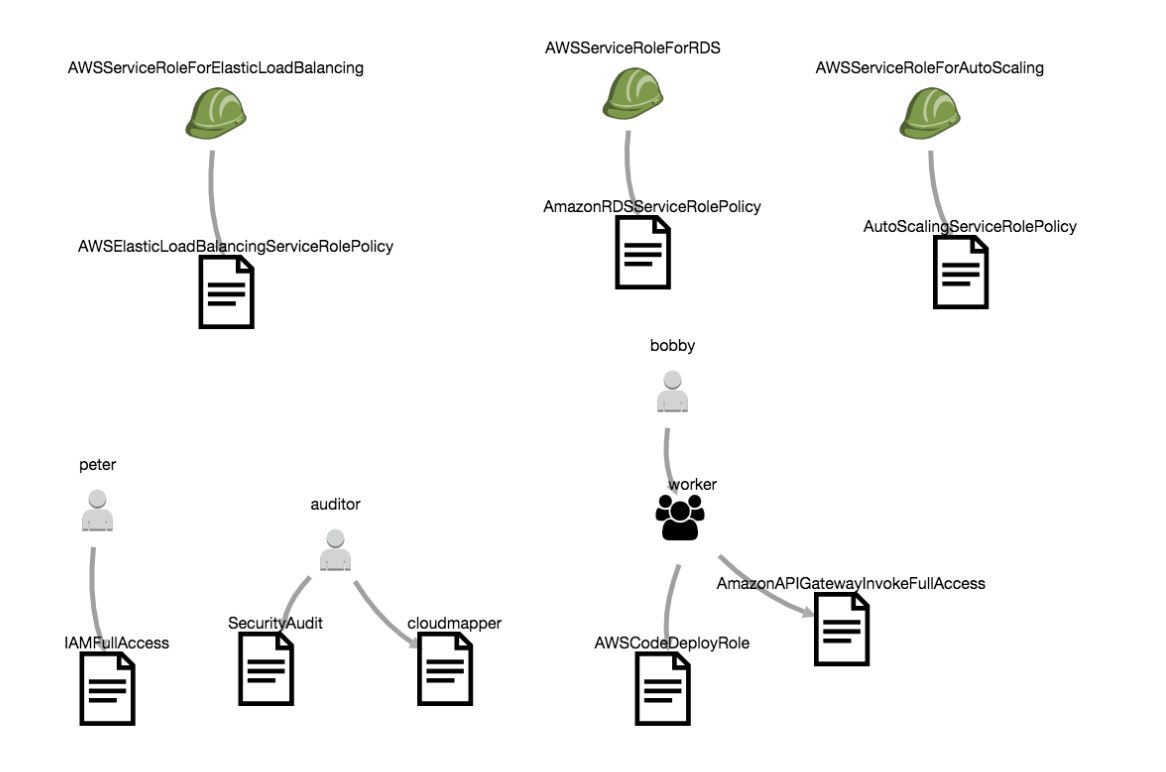
One special feature of this report is the ability to generate a graph with the --graph option that will show how membership and attachment links between users, roles, groups, and policies. This is often over-whelming, but can be useful for spotting oddities.