CloudMapper has had an audit command for a while now, which is a great way to look for security misconfigurations. This would print out text like this:
$ python cloudmapper.py audit --account test
LOW - test (us-east-1) - Password policy is not set: None
LOW - test (us-east-1) - User has unused access key: bobby
Findings in report
The text output of the audit command has been good enough for most of my needs in helping perform some of the automated checks in an assessment, but if you’ve been following me on twitter (@0xdabbad00) you might have seen some screenshots of work I’ve been up to on making the report command more featureful. The HTML report that CloudMapper generates now include audit findings and related charts!
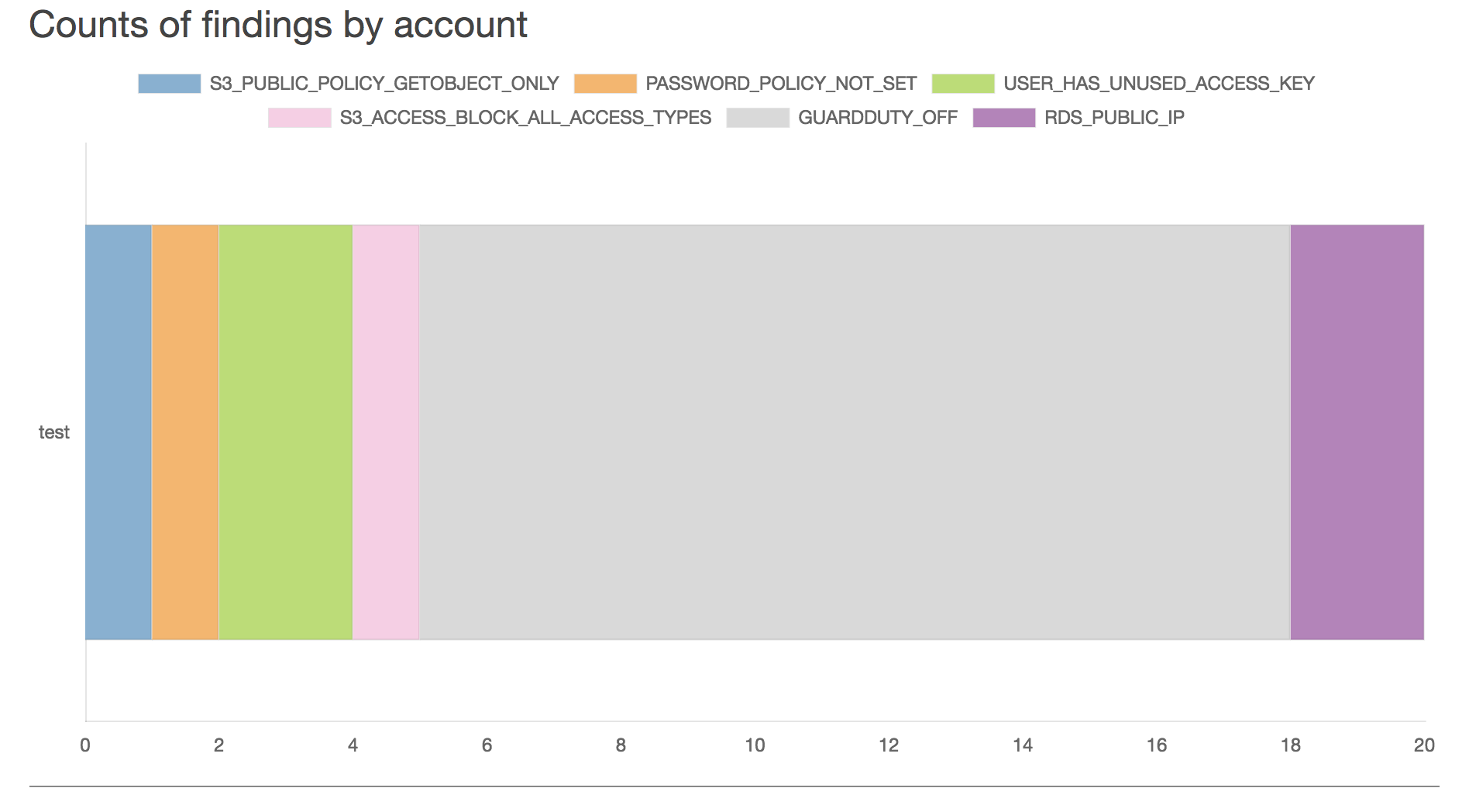
The above chart shows the counts of types of findings, colored by severity, for each account. This helps you quickly identify the accounts that need the most work or the ones with the highest severity findings. Below that are links to the types of findings.
Next the report shows the counts of individual findings, colored by each type for each account. This is helpful for determining how much work is going to be involved in fixing the issues. For example, an account with one unused access key and an account with a 100 unused access keys would each show up the same on the first findings chart because it is only one issue type, but in this next chart, it would show the second account as having 100x more findings.
Finally the report gives a description of the finding type and details on the resources that matched this finding, broken up by account, and where it makes sense, by region.
Demo
Click here for a demo of the report command.
json output for audit findings
The audit command has also been updated to include a --json flag so you can output the results as json for feeding into another tool. This creates the opportunity to perform daily CloudMapper collection and auditing of your accounts, sending any issues found to Slack or similar.
$ python cloudmapper.py audit --account test --json
{"account_id": "954574370272", "account_name": "test", "region": "us-east-1", "issue": "PASSWORD_POLICY_NOT_SET", "resource": null, "details": null}
{"account_id": "954574370272", "account_name": "test", "region": "us-east-1", "issue": "USER_HAS_UNUSED_ACCESS_KEY", "resource": "bobby", "details": {"Unused key": 1}}
Documenting finding types
In order to enable this new functionality, the findings that are looked for have been documented at https://github.com/duo-labs/cloudmapper/blob/master/audit_config.yaml
Currently, 37 types of issues are audited for, and this file makes it easier to read through what these issues are.